Douglas Stebila
Multi-factor password-authenticated key exchange
Abstract
We consider a new form of authenticated key exchange which we call multi-factor password-authenticated key exchange, where session establishment depends on successful authentication of multiple short secrets that are complementary in nature, such as a long-term password and a one-time response, allowing the client and server to be mutually assured of each other's identity without directly disclosing private information to the other party.
Multi-factor authentication can provide an enhanced level of assurance in higher-security scenarios such as online banking, virtual private network access, and physical access because a multi-factor protocol is designed to remain secure even if all but one of the factors has been compromised.
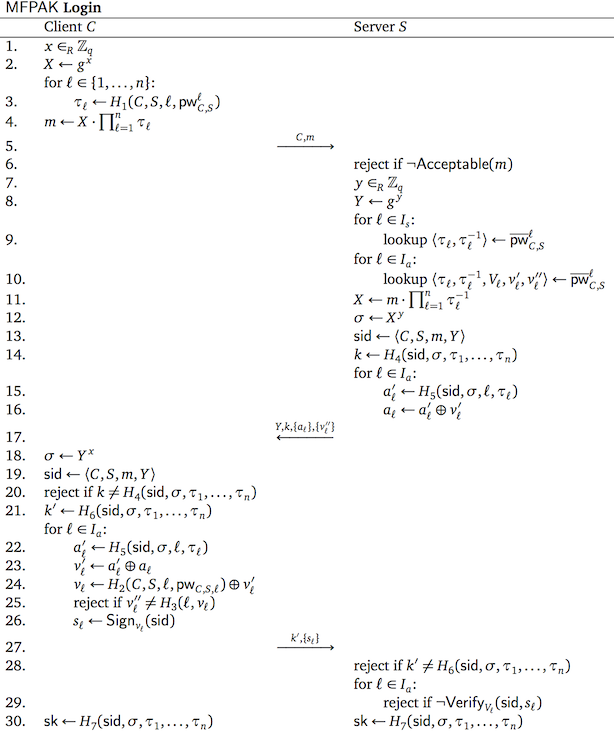
We introduce a security model for multi-factor password-authenticated key exchange protocols, propose an efficient and secure protocol called MFPAK, and provide a security argument to show that our protocol is secure in this model. Our security model is an extension of the Bellare-Pointcheval-Rogaway security model for password-authenticated key exchange and accommodates an arbitrary number of symmetric and asymmetric authentication factors.
Keywords: multi-factor authentication, passwords, key exchange, cryptographic protocols
Reference
Douglas Stebila, Poornaprajna Udupi, Sheueling Chang. Multi-factor password-authenticated key exchange. In Colin Boyd, Willy Susilo, editors, Proc. 8th Australasian Information Security Conference (AISC) 2010, Conferences in Research and Practice in Information Technology, vol. 105, pp. 56-66. Australian Computer Society, January 2010. © Australian Computer Society.
Download
Presentations
- 2010-01-20: AISC 2010. (PDF slides)
BibTeX
Funding
This research was supported by:- NSERC Canada Graduate Scholarship