Douglas Stebila
A cryptographic analysis of the TLS 1.3 draft-10 full and pre-shared key handshake protocol
Abstract
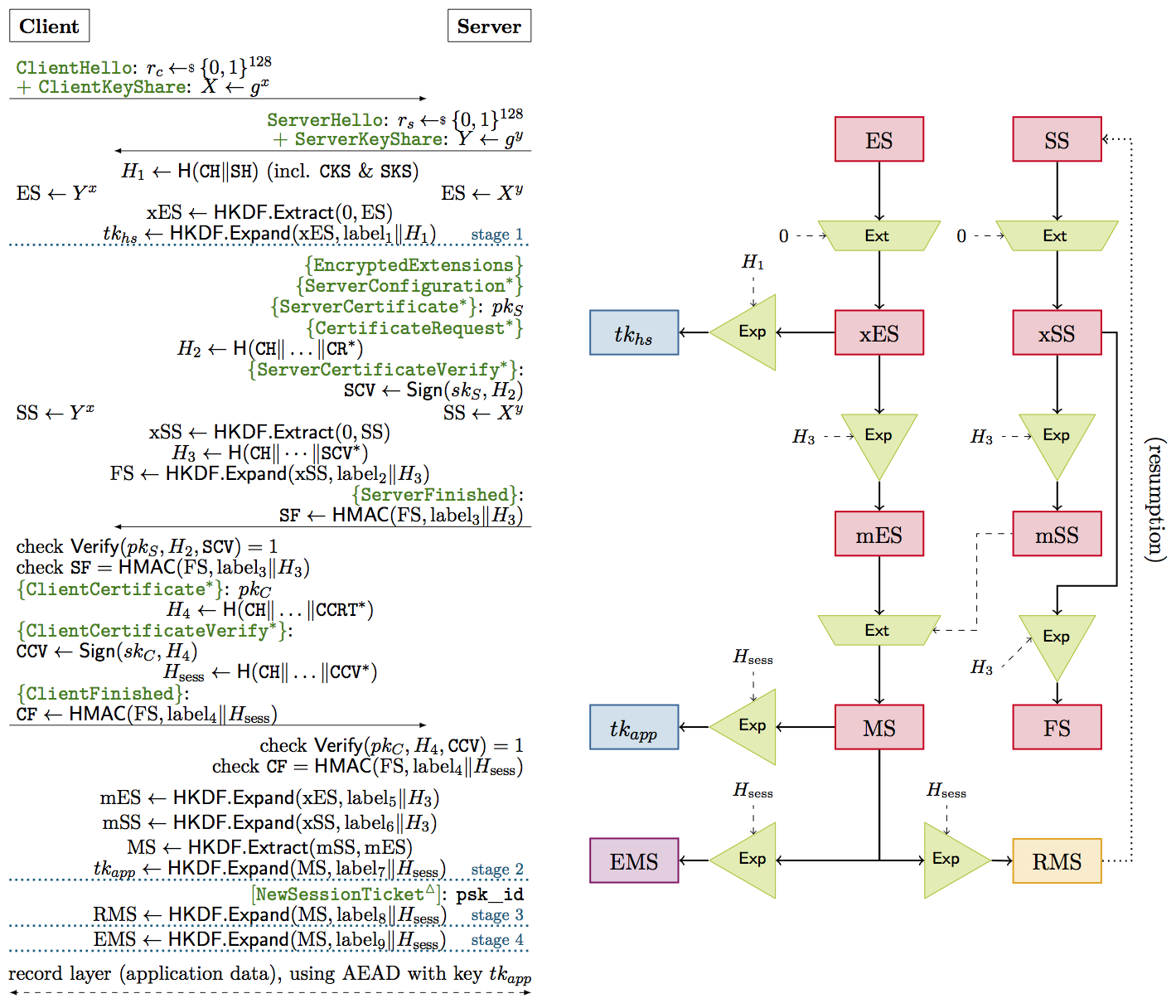
We analyze the handshake protocol of TLS 1.3 draft-ietf-tls-tls13-10 (published October 2015). This continues and extends our previous analysis (CCS 2015, Cryptology ePrint Archive 2015) of former TLS 1.3 drafts (draft-ietf-tls-tls13-05 and draft-ietf-tls-tls13-dh-based). Here we show that the full (EC)DHE Diffie-Hellman-based handshake of draft-10 is also secure in the multi-stage key exchange framework of Fischlin and Günther which captures classical Bellare-Rogaway key secrecy for key exchange protocols that derive multiple keys.
We also note that a recent protocol change—the introduction of a NewSessionTicket message for resumption, encrypted under the application traffic key—impairs the protocol modularity and hence our compositional guarantees that ideally would allow an independent analysis of the record protocol. We additionally analyze the pre-shared key modes (with and without ephemeral Diffie-Hellman key), and fit them into the composability framework, addressing composability with the input resumption secret from a previous handshake and of the output session keys.
Keywords: Transport Layer Security (TLS), key exchange, protocol analysis, composition
Reference
Benjamin Dowling, Marc Fischlin, Felix Günther, Douglas Stebila. A cryptographic analysis of the TLS 1.3 draft-10 full and pre-shared key handshake protocol. Technical report. January 2016. Presented at the TLSv1.3 Ready or Not (TRON) Workshop held at the Network and Distributed Security Symposium (NDSS) 2016..
Download
BibTeX
Funding
This research was supported by:- Australian Research Council (ARC) Discovery Project grant DP130104304
- Heisenberg grant Fi 940/3-2 of the German Research Foundation (DFG) as part of project S4 within the CRC~1119 CROSSING