Douglas Stebila
Elliptic curve cryptography on Google
December 1, 2011 at 01:06PM Research
Ten years ago, in September 2001, I started working at Sun Microsystems Laboratories, on a project to integrate a new form of cryptography, elliptic curve cryptography (ECC), in the web's security infrastructure (the SSL/TLS protocol). There were several milestones along the way: the first contribution of our code to the OpenSSL and Mozilla projects in 2002 and 2003, publications describing our work in top security conferences, interoperability testing in 2005/2006, the official conclusion of the Sun Labs project around 2005, and the final publication of the standard defining the use of ECC in TLS in 2008. Our code can be found on literally billions of computers worldwide: in every version of Mozilla Firefox (type about:credits to see my name!), every version of Google Chrome, every version of the Apache web server, and on every Mac and Linux computer.
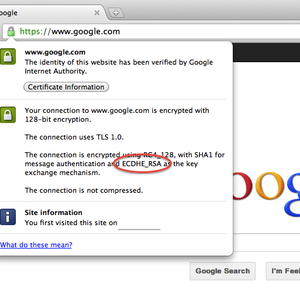
This past week another major milestone in the deployment of elliptic curve cryptography has happened: Google has enabled the use of ECC on its secure web pages as the default algorithm. (More precisely, the ECDHE_RSA_RC4_SHA cipher suite is the default cipher suite.) As far as I know, this is the first large scale site to enable ECC. Google has for some time been leading efforts on improving the speed and effectiveness of security protocols on the web.If you use Firefox or Chrome, your web browser will automatically use ECC whenever you visit a secure Google page. The main benefit of this technology is that your data is encrypted using a temporary key, rather than a permanent key, so even if Google's permanent key is compromised in the future, your past communications will remain secure (this is called "forward secrecy"). Elliptic curve cryptography is quite fast, so it can do this with adding very little computational burden to your computer, so you shouldn't notice any performance impact from this enhanced security.
For more information, check out the official Google security blog post as well as more details from one of the Google engineers.