Douglas Stebila
Denial of service paper
April 21, 2009 at 02:10AM Research
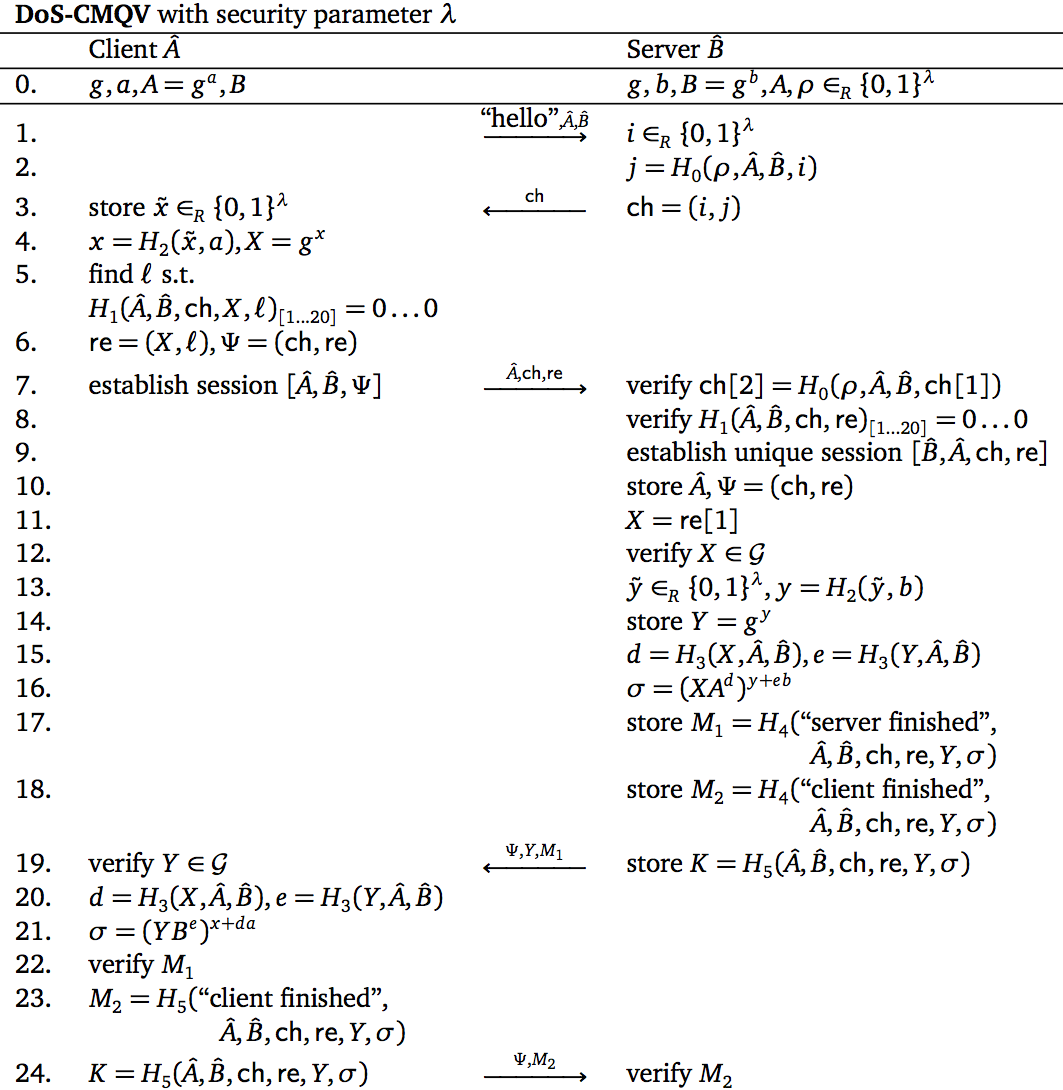
I'm pleased to announce that some of the work that appeared in my PhD thesis has recently been accepted to a conference. My work with fellow University of Waterloo student Berkant Ustaoglu (now a postdoc at NTT in Tokyo) on denial-of-service-resilient key agreement protocols will be presented at the 14th Australasian Conference on Information Security and Privacy (ACISP) 2009 which is being held here in Brisbane in July, and the proceedings will be published in Springer's Lecture Notes in Computer Science.Denial of service attacks are where an attacker tries to consume all the resources that a computer, such as a web server, has available -- filling up all of its memory or overloading its processor, for example. One of the most expensive operations that a web server performs is the cryptographic key agreement protocol, where it sets up a secure channel between the user's computer and the web server.
Before doing expensive operations like cryptography or database lookups, a server could request that the user "prove" it's not trying to cause trouble. One way of doing so is to give the user's computer a puzzle to solve, something that might take the user's computer a couple of seconds of hard work to solve, but the solution to which can be verified instantaneously by the server. This way, an attacker has to do a lot of work to create many requests to overload the web server, but a normal user is not too burdened by this requirement. These techniques have been known for some time, but how they should be used has only been studied in an ad hoc fashion.
Our work develops a formal mathematical model for how cryptographic communication protocols should try to resist denial of service attacks by using puzzles, similar to the formal mathematical models for the confidentiality of key agreement. We give a protocol that achieves these goals, and more importantly our framework could be used by many protocols to describe their denial of service resistance properties.
The main project I am working on during my postdoc here at QUT is further studying how to model denial of service, so this paper has been a great start to my work down here.