Douglas Stebila
Post-quantum key-blinding for authentication in anonymity networks
Abstract
Anonymity networks, such as the Tor network, are highly decentralized and make heavy use of ephemeral identities. Both of these characteristics run in direct opposition to a traditional public key infrastructure, so entity authentication in an anonymity network can be a challenge. One system that Tor relies on is key-blinded signatures, which allow public keys to be transformed so that authentication is still possible, but the identity public key is masked. This is used in Tor during onion service descriptor lookup, in which a .onion address is resolved to a rendezvous point through which a client and an onion service can communicate. The mechanism currently used is based on elliptic curve signatures, so a post-quantum replacement will be needed.
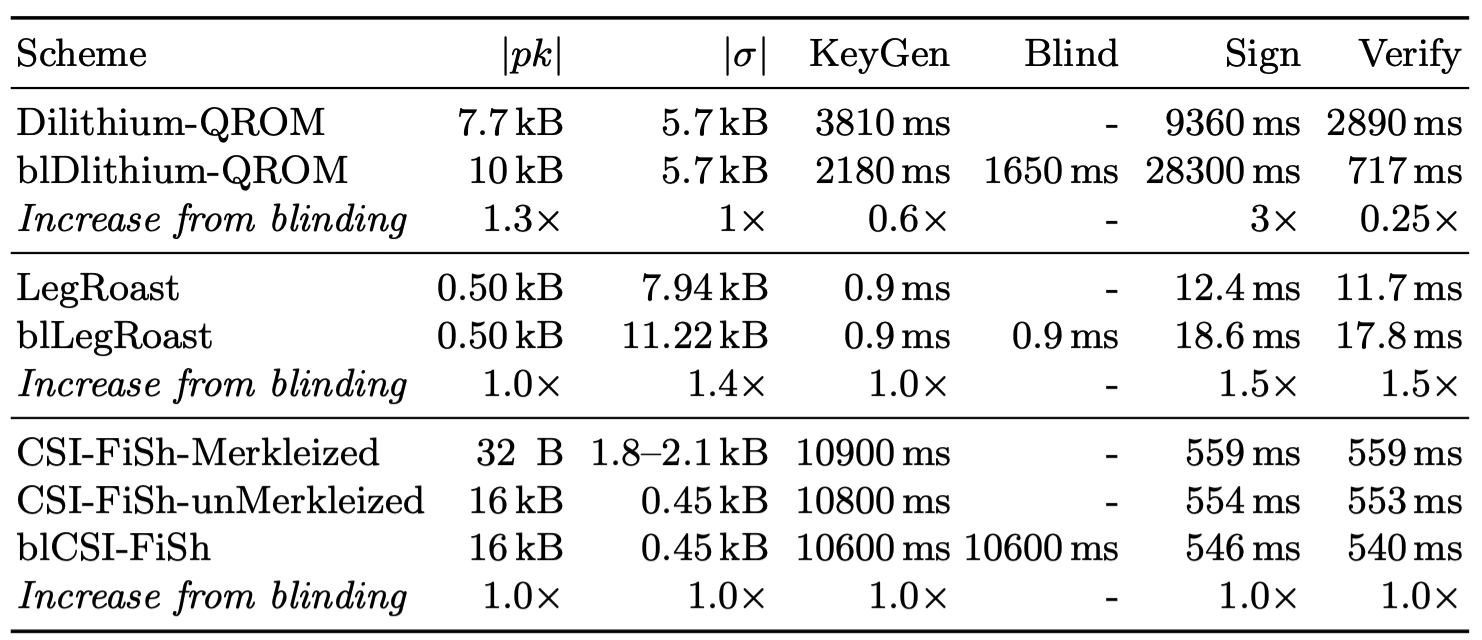
We consider four fully post-quantum key-blinding schemes, and prove the unlinkability and unforgeability of all schemes in the random-oracle model. We provide a generic framework for proving unlinkability of key-blinded schemes by reducing to two properties, signing with oracle reprogramming and independent blinding. Of the four schemes, two are based on Round 3 candidates in NIST's post-quantum signature standardization process, Dilithium and Picnic. The other two are based on much newer schemes, CSI-FiSh and LegRoast, which have more favourable characteristics for blinding. CSI-FiSh is based on isogenies and boasts a very small public key plus signature sizes, and its group action structure allows for key-blinding in a straightforward way. LegRoast uses the Picnic framework, but with the Legendre symbol PRF as a symmetric primitive, the homomorphic properties of which can be exploited to blind public keys in a novel way. Our schemes require at most small changes to parameters, and are generally almost as fast as their unblinded counterparts, except for blinded Picnic, for which signing and verifying is roughly half as fast.
Keywords: digital signatures, post-quantum cryptography, key blinding
Reference
Edward Eaton, Douglas Stebila, Roy Stracovsky. Post-quantum key-blinding for authentication in anonymity networks. In Patrick Longa, Carla Ràfols, editors, Proc. 7th International Conference on Cryptology and Information Security in Latin America (LATINCRYPT) 2021, LNCS, vol. 12912, pp. 67-87. Springer, October 2021. © Springer.
Download
Code
BibTeX
Funding
This research was supported by:- Natural Sciences and Engineering Research Council of Canada (NSERC) Discovery grant RGPIN-2016-05146