Douglas Stebila
On the security of TLS renegotiation
Abstract
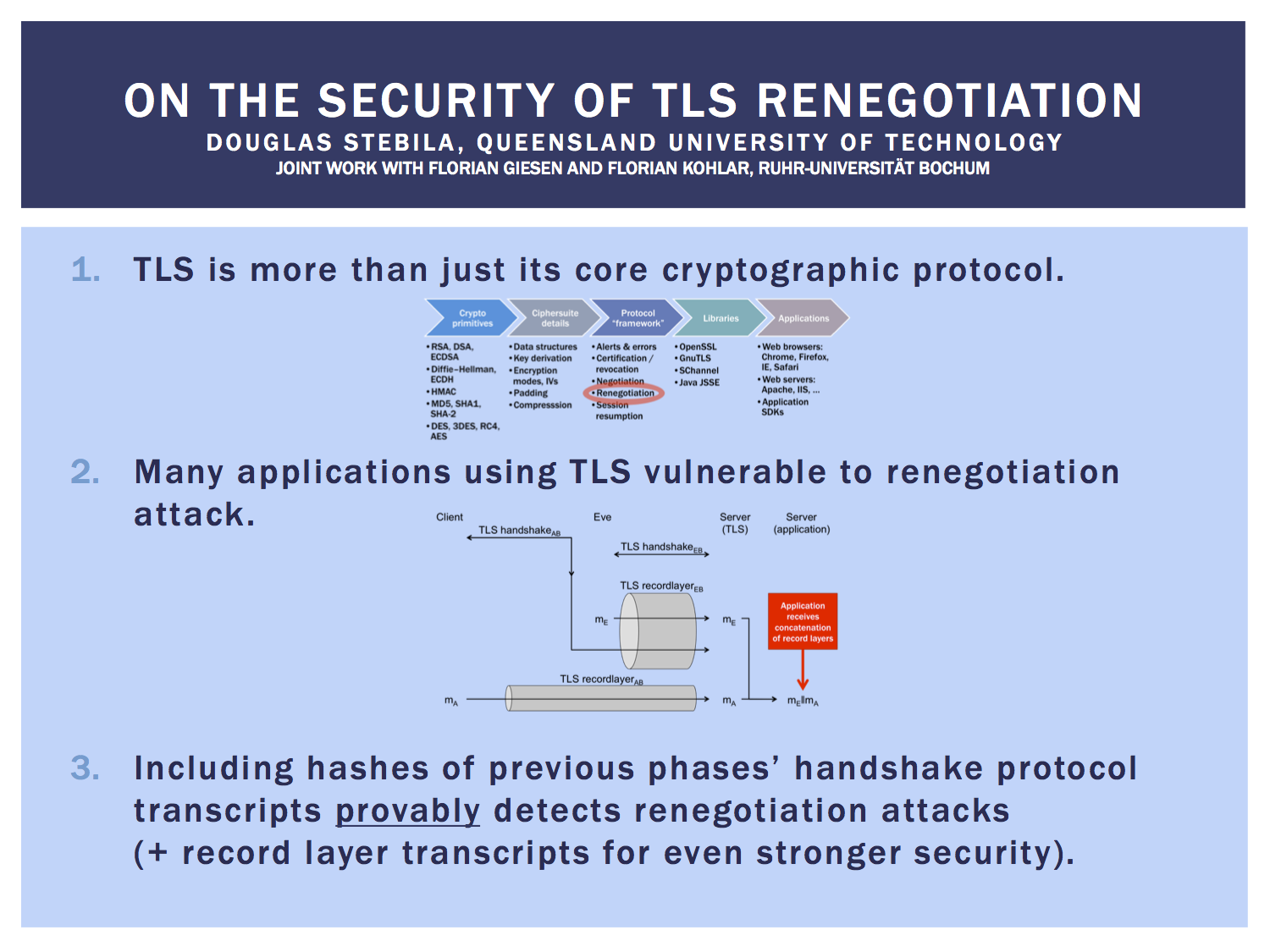
The Transport Layer Security (TLS) protocol is the most widely used security protocol on the Internet. It supports negotiation of a wide variety of cryptographic primitives through different cipher suites, various modes of client authentication, and additional features such as renegotiation. Despite its widespread use, only recently has the full TLS protocol been proven secure, and only the core cryptographic protocol with no additional features. These additional features have been the cause of several practical attacks on TLS. In 2009, Ray and Dispensa demonstrated how TLS renegotiation allows an attacker to splice together its own session with that of a victim, resulting in a man-in-the-middle attack on TLS-reliant applications such as HTTP. TLS was subsequently patched with two defence mechanisms for protection against this attack.
We present the first formal treatment of renegotiation in secure channel establishment protocols. We add optional renegotiation to the authenticated and confidential channel establishment model of Jager et al., an adaptation of the Bellare--Rogaway authenticated key exchange model. We describe the attack of Ray and Dispensa on TLS within our model. We show generically that the proposed fixes for TLS offer good protection against renegotiation attacks, and give a simple new countermeasure that provides renegotiation security for TLS even in the face of stronger adversaries.
Keywords: Transport Layer Security (TLS), renegotiation, security models, key exchange
Reference
Florian Giesen, Florian Kohlar, Douglas Stebila. On the security of TLS renegotiation. In Virgil Gligor, Moti Yung, editors, Proc. 20th ACM Conference on Computer and Communications Security (CCS) 2013, pp. 387-398. ACM, November 2013. © ACM.
Download
Presentations
- 2014-09-22: University of Waterloo Centre for Applied Cryptographic Research. (PDF slides)
- 2014-09-09: Gjøvik University College, Norway.
- 2014-07-18: Microsoft Research Redmond. (PDF slides)
- 2014-06-03: Secure Key Exchange and Channels Workshop 2014, Bertinoro, Italy. More technical version of January 2014 talk below (PDF slides)
- 2014-01-14: Real World Cryptography 2014. Less technical version of June 2014 talk above (PDF slides)
- 2013-11-05: ACM CCS 2013. (PDF slides)
- 2012-11-02: QUT Information Security Colloquium. (PDF slides)
- 2012-10-04: Royal Holloway, University of London.
BibTeX
Funding
This research was supported by:- Australian Research Council (ARC) Discovery Project grant DP130104304
- the Australian Technology Network–German Academic Exchange Service (ATN-DAAD) Joint Research Co-operation Scheme
- the European Community (FP7/2007-2013) under grant agreement number ICT-2007-216646 - European Network of Excellence in Cryptology II (ECRYPT II)